Secure passwords.
The number of your user accounts increases daily. A separate password is required for each account. Using passwords more than once is insecure. Password databases are stored in the cloud or require complex backups.
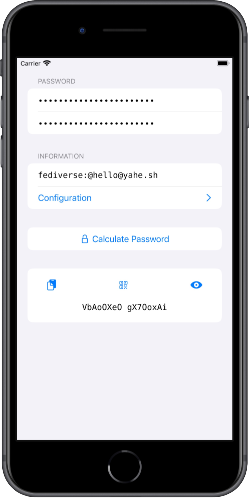
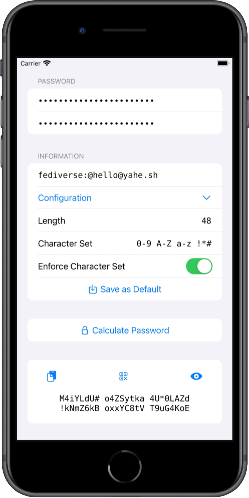
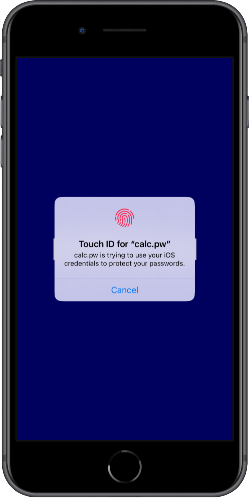
calc.pw offers an alternative: From a single master password and an easily derivable information like your username or the web address, any number of passwords can be generated - simple, local and secure based on the established crypto algorithms AES-256 and SHA-256.
By entering the same master password and the same information calc.pw calculates the same password again. There is no need to backup passwords or synchronize them through the cloud.
Secure passwords. Always and everywhere.